What is Zero Trust Security Model ?
The security landscape has undergone a substantial transition in an era marked by the quick development of digital technologies and the smooth integration of cloud computing into everyday company activities. The dynamic nature of contemporary IT infrastructures and sophisticated cyber threats have rendered traditional security methods, which formerly placed a strong emphasis on perimeter defenses, inadequate. This calls for a fundamental change in strategy in favor of the Zero Trust Security Model, which is more robust and adaptable.
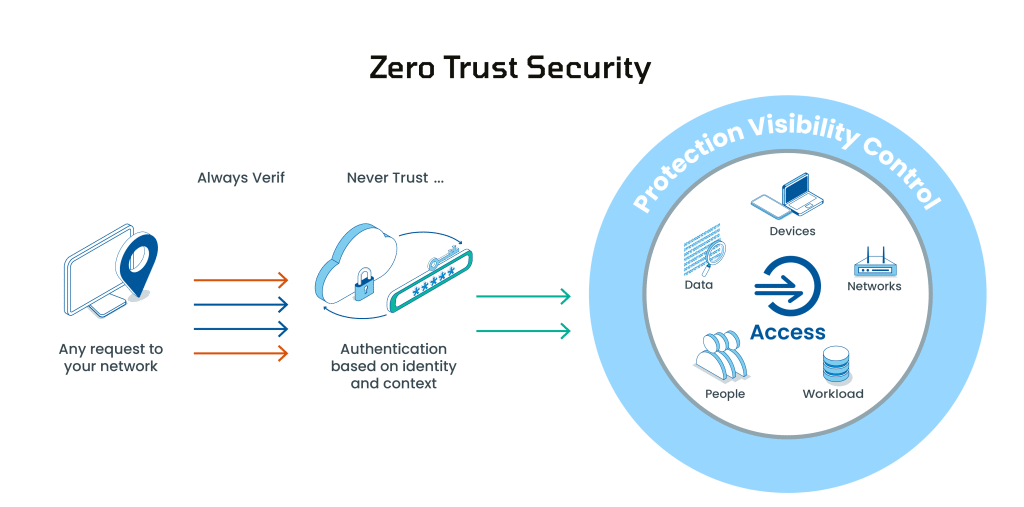
Zero Trust Security Model is a methodology that eliminates the notion of automatic trust within network systems, applications, and data protection. This stands in sharp contrast to the conventional perimeter security model, which operates on the assumption that potential threats exist solely outside the trusted network perimeter, while internal users are inherently trustworthy. In the realm of Zero Trust, these assumptions are overturned, and every user is treated as untrustworthy, challenging the traditional notions of trust and skepticism in cybersecurity.
As per Forrester Research, a prominent research and advisory organization, a Zero Trust solution should adhere to the following principles:
- Implement strict segmentation and enable Layer 7 policies to permit only known and authorized traffic or legitimate application communication.
- Employ a least-privileged access strategy and rigorously enforce access control measures.
- Conduct thorough inspection and logging of all traffic. Neglecting this step could potentially create vulnerabilities, allowing attackers to easily gain access to a company’s network.
Beyond simply deploying a security gateway, cloud environments must adopt a sophisticated and all-encompassing strategy to implement the Zero Trust Security Model. Although the fundamental principle of directing access through a security gateway for secure least-privileged access is still important, it is critical to understand that the complexity of cloud ecosystems necessitates a more complex approach. To truly deploy Zero Trust, every traffic across all applications must be carefully examined, simply implementing a gateway is not enough.
How Zero Trust Model Works ?
The implementation of this framework integrates cutting-edge technologies, including risk-based multi-factor authentication, identity protection, next-generation endpoint security, and resilient cloud workload technology. These technologies collectively verify the identity of a user or system, take into account the access context at the specific moment, and ensure the ongoing maintenance of system security. Zero Trust also mandates the implementation of data encryption, the secure handling of email, and the verification of the cleanliness of assets and endpoints before establishing connections to applications.
The Zero Trust architecture mandates organizations to consistently assess and verify the appropriateness of a user and their device’s privileges and attributes. It necessitates the implementation of policies that take into account the risk associated with both the user and the device, in addition to compliance and other prerequisites, before authorizing any transaction. Furthermore, organizations must possess comprehensive knowledge of all their service and privileged accounts, establishing controls to govern their connections and locations. A one-time validation approach is insufficient since threats and user attributes are susceptible to change.
Consequently, organizations are compelled to subject all access requests to ongoing scrutiny before granting entry to enterprise or cloud assets. This underscores the reliance on real-time visibility into hundreds of user and application identity attributes for the effective enforcement of Zero Trust policies.
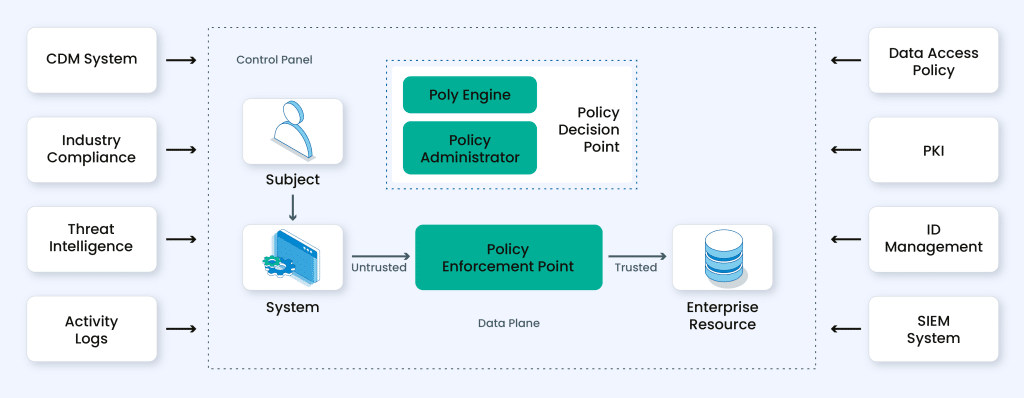
In the intricate web of Zero Trust Security Model, various components interplay to create a robust defense. Let’s explore the elements that constitute this dynamic approach:
Credential Information:
Understanding the intricacies of user identity and the type of credential (human or programmatic) is fundamental. This information sets the foundation for access privileges and is a cornerstone of the Zero Trust model.
Credential Privileges:
The access landscape is further defined by credential privileges on each device. By scrutinizing and restricting access based on user credentials, organizations ensure that only authorized entities navigate the digital terrain.
Connection Patterns:
Normal connections for the credential and device, exhibited through behavior patterns, are crucial. Detecting anomalies in these patterns allows for proactive measures, thwarting potential security threats before they escalate.
Endpoint Hardware:
Understanding the endpoint hardware type and function adds another layer to the security matrix. Differentiating between hardware configurations contributes to a nuanced approach in securing devices.
Geo-location Factors:
Considering the geographical location of the user or device is pivotal. This aspect provides context to access requests, aiding in the determination of legitimacy and enhancing the overall security posture.
Firmware Versions:
The firmware versions on devices play a role in the Zero Trust framework. Ensuring that firmware is up-to-date is imperative for closing potential vulnerabilities and maintaining a resilient security infrastructure.
Authentication Protocols and Risk:
Delving into authentication protocols and associated risks helps in gauging the strength of access points. Analyzing potential risks associated with specific protocols enhances the security model’s effectiveness.
Operating System Details:
Knowledge of operating system versions and patch levels is paramount. Regular updates and patches contribute to a robust defense mechanism, preventing exploitation of known vulnerabilities.
Applications on Endpoints:
Understanding the applications installed on endpoints is vital for security. Each application introduces a potential avenue for exploitation, making it essential to manage and monitor them closely.
Security Detections:
Finally, security or incident detections, including recognition of suspicious activity and potential attacks, complete the picture. Real-time monitoring and response capabilities are critical in swiftly addressing any security incidents.
In the dynamic realm of Zero Trust, weaving these components together creates a comprehensive security fabric, empowering organizations to navigate the evolving threat landscape with resilience and agility.
Zero Trust vs VPN
Zero Trust and Virtual Private Network (VPN) technologies play pivotal roles in a robust cybersecurity strategy, each fulfilling distinct functions and employing unique methodologies. Let’s delve into the key distinctions between Zero Trust and VPN.
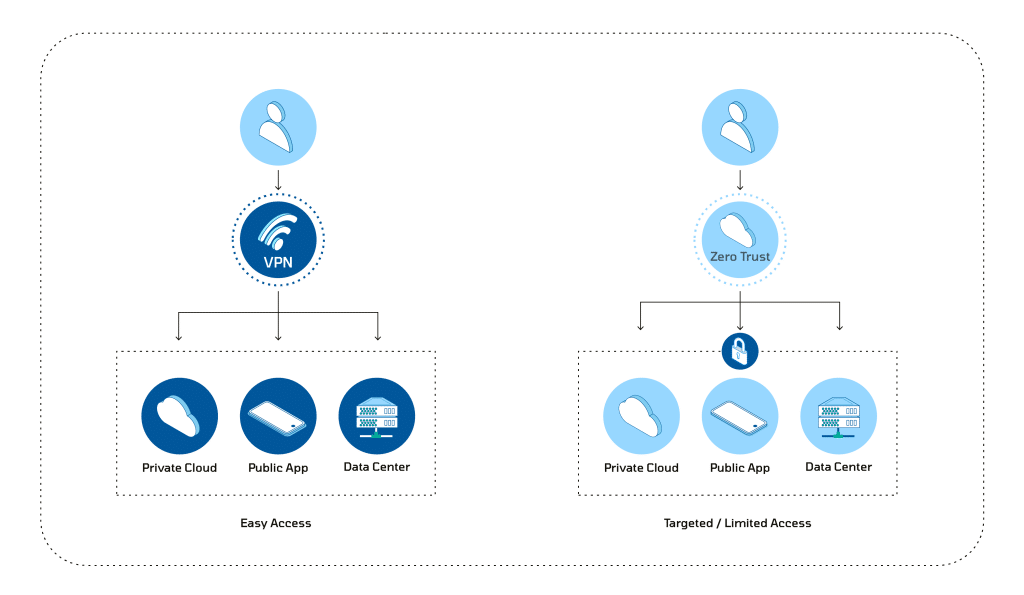
Zero Trust
Philosophy:
Zero Assumption of Trust: Zero Trust operates under the guiding principle of “never trust, always verify.” It challenges the conventional practice of relying on the location of entities within the network and instead mandates continuous verification of identities and devices, irrespective of their geographical location.
Access Control:
Least Privilege Access: Zero Trust places a strong emphasis on granting the minimum level of access necessary for users, devices, and applications to execute their functions. Access levels are dynamically adjusted based on real-time assessments of security posture and user behavior.
Dynamic Verification:
Continuous Authentication: Zero Trust hinges on continuous authentication and authorization. This entails users and devices being authenticated at each access attempt, ensuring an ongoing and dynamic verification process that thwarts unauthorized access and lateral movement within the network.
Network Segmentation:
Micro-Segmentation: Zero Trust frequently employs network segmentation at a granular level. This involves dividing the network into smaller segments to contain potential threats effectively. Such micro-segmentation ensures that even if one segment is compromised, the lateral movement of attackers is confined.
VPN (Virtual Private Network):
Connectivity:
Ensuring Secure Remote Access: VPNs establish a secure and encrypted connection over the internet, enabling remote users or branch offices to securely connect to the organization’s internal network. This is particularly crucial for preserving privacy and security when accessing sensitive data over public networks.
Perimeter-Based Security:
Reinforcing the Network Perimeter: VPNs traditionally uphold the notion of a network perimeter. Once a user establishes a VPN connection, they are treated as an integral part of the internal network, with trust often assumed based on this connection.
Access Control:
Full Network Access: VPNs generally grant access to the entire internal network for authenticated users. While measures for access control can be implemented, they might not exhibit the same level of dynamism or granularity as those found in a Zero Trust model.
Use Case:
Facilitating Secure Remote Work: VPNs are frequently employed to support secure remote work scenarios, enabling employees to securely access corporate resources from external locations. This is achieved by encrypting the communication between the user and the internal network.